Streamlining Security: The Importance of User Access Reviews
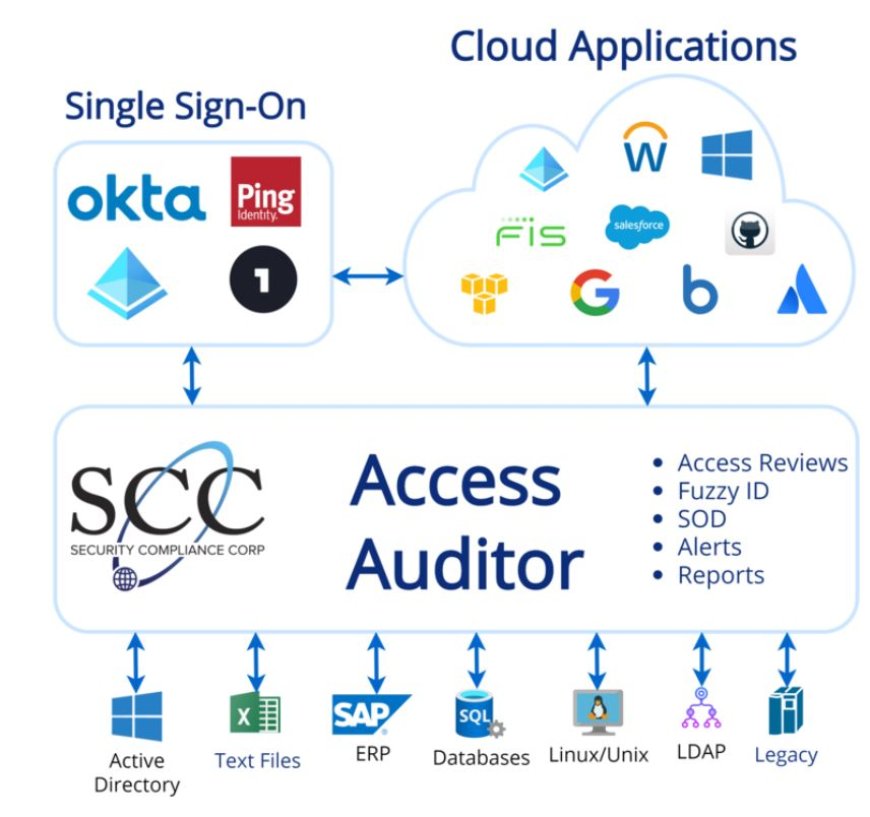
Introduction:
In the ever-evolving landscape of cybersecurity, maintaining robust defenses against potential threats is paramount. One crucial aspect of cybersecurity is user access management, which involves controlling and monitoring the access that users have to organizational resources and sensitive information. User access reviews play a vital role in this process, ensuring that access rights remain appropriate and secure. In this article, we'll explore the importance of user access reviews in streamlining security and mitigating risks within organizations.

Understanding User Access Reviews:
User access reviews, also known as access recertifications or entitlement reviews, are periodic assessments conducted to verify and validate the access rights assigned to users within an organization. These reviews involve examining user permissions, roles, and entitlements to ensure that they align with the principle of least privilege – granting users only the permissions necessary to perform their job functions. By conducting regular access reviews, organizations can identify and address inappropriate access, reduce the risk of data breaches, and maintain compliance with regulatory requirements.
The Importance of Streamlining Security:
Effective security measures are essential for safeguarding sensitive data, protecting against cyber threats, and maintaining the trust of customers and stakeholders. User access reviews play a critical role in streamlining security by ensuring that access controls are properly configured, access rights are up-to-date, and unauthorized access is promptly detected and remediated. By streamlining security processes through regular access reviews, organizations can proactively identify and mitigate security risks, reduce the likelihood of security incidents, and minimize the impact of potential breaches.
Key Benefits of User Access Reviews:
-
Risk Mitigation: User access reviews help organizations identify and mitigate security risks associated with excessive or inappropriate access rights. By regularly reviewing user permissions and entitlements, organizations can minimize the risk of insider threats, data breaches, and unauthorized access to sensitive information.
-
Compliance Assurance: Many regulatory frameworks and industry standards require organizations to implement controls for managing user access and enforcing segregation of duties. User access reviews help organizations demonstrate compliance with these requirements by providing evidence of ongoing access control assessments and remediation efforts.
-
Operational Efficiency: Streamlining security processes through regular user access reviews can enhance operational efficiency by optimizing access controls, reducing administrative overhead, and automating repetitive tasks. By implementing efficient access review workflows and leveraging technology solutions, organizations can streamline security operations and improve resource utilization.
-
Cost Savings: Proactively managing user access through regular reviews can help organizations avoid potential costs associated with security incidents, data breaches, and regulatory non-compliance. By identifying and remedying access issues before they escalate into larger problems, organizations can minimize financial losses and reputational damage.
Best Practices for Conducting User Access Reviews:
To maximize the effectiveness of user access reviews, organizations should follow best practices such as:
-
Establishing clear access review policies and procedures
-
Defining roles and responsibilities for conducting reviews
-
Leveraging technology solutions for automating access review workflows
-
Regularly communicating access review requirements to relevant stakeholders
-
Documenting review activities, findings, and remediation efforts
-
Conducting periodic audits to assess the effectiveness of access review processes
Conclusion:
User access reviews play a critical role in streamlining security within organizations by ensuring that access rights are appropriate, secure, and compliant. By conducting regular access reviews, organizations can proactively identify and mitigate security risks, maintain compliance with regulatory requirements, and enhance operational efficiency. As cybersecurity threats continue to evolve, user access reviews remain an essential component of a comprehensive security strategy, helping organizations stay ahead of emerging threats and safeguarding their most valuable assets.

 jameswatkin
jameswatkin 





